Custom Maid 3D is an Adventure game, developed and published by Kiss, which was released in Japan in 2011. Free Shipping. Save this search. New Custom Maid 3D 2 Windows PC Game KISS Japan Anime Cute Girl Japanese F/S See more like this.  Custom Maid 3D 2: Technical Help. Then try to download the patch again from the official site. Explained in NPC Maid VIP. Q11: My game system don't have free. KISS Custom Maid 3D Complete Pack Windows PC Game DVD-ROM F/S w/Tracking# Japan See more like this SPONSORED Custom Maid 3D2+ KISS Windows PC Game Anime Cosplay Free Shipping.
Custom Maid 3D 2: Technical Help. Then try to download the patch again from the official site. Explained in NPC Maid VIP. Q11: My game system don't have free. KISS Custom Maid 3D Complete Pack Windows PC Game DVD-ROM F/S w/Tracking# Japan See more like this SPONSORED Custom Maid 3D2+ KISS Windows PC Game Anime Cosplay Free Shipping.
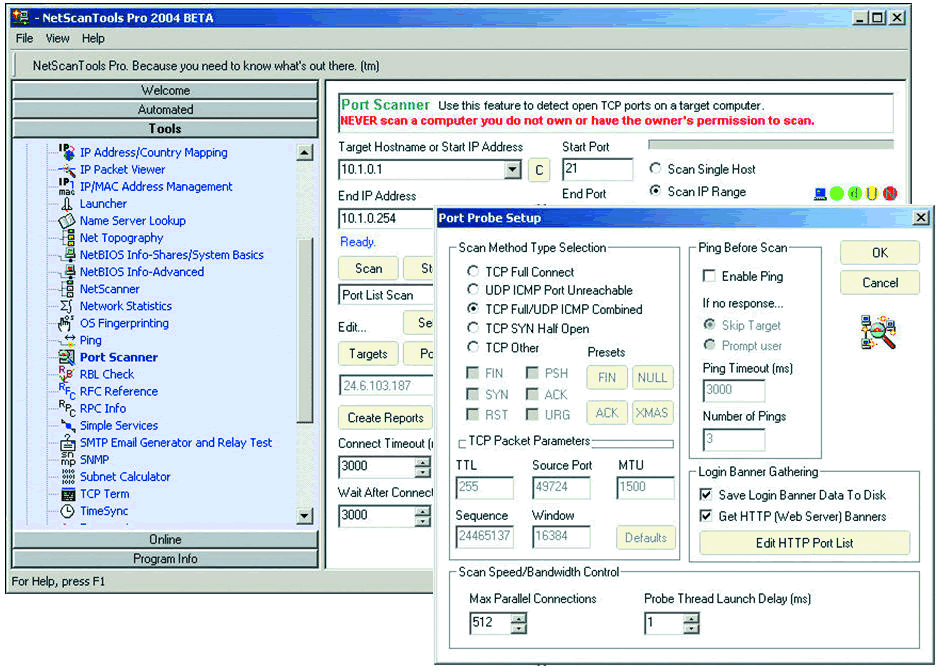
NetScanTools Pro, an advanced internet information gathering toolkit for use on the Windows Operating System.
Zedload.com provides 24/7 fast download access to the most recent releases. We currently have 276,088 full downloads including categories such as: software, movies, games, tv, adult movies, music, ebooks, apps and much more. Our members download database is updated on a daily basis. Take advantage of our limited time offer and gain access to unlimited downloads for FREE! That's how much we trust our unbeatable service. This special offer gives you full member access to our downloads. Click to the Zedload today for more information and further details to see what we have to offer.
Laura Chappell 01 May 2004 This article defines some of the tools which students use in the 'White Hat Toolbox' hands-on course that tours around the United States and Europe in 2004. (Visit for more information.) Be certain you have permission from the owner of the target system (preferably in writing) before you perform password-integrity tests, port scans, vulnerability scans or any other communication that might be deemed intrusive. I must admit, my heart skips a beat or two each BrainShare when I look out at the line of eager techies waiting to scan their badges, take their seats and watch the Hot Tools class.
This was the third year I'd presented this course at BrainShare and I admit--it is my favorite course to teach! Essentially, we throw out the slide presentation (my apologies to the graphic design team) and we start working live on the network. It is always a blast to start playing on the show network with vulnerability scanners, interceptors and redirectors, packet generators and forensic tools. Once we took over a security camera and found a guy who had access to a shared directory that really shouldn't have been shared (yipes!).
We've found assorted open systems (and I don't mean that in a nice 'open source' sort of way) and a few print servers without passwords. If you found those hosts on your network, you would probably shut them down in no time. With the right tools, you can easily find these lapses in your systems and address them.
In addition, with the right tools, you should be able to troubleshoot network communications, locate unsecure systems, identify unsecure applications and trace back to an attacker. These tools should allow you to test systems in your lab, check how an Intrusion Detection System (IDS) handles unacceptable traffic and even note when a user is scanning the network (and hitting your decoy along the way). Who says networking is boring? We are in the right field at the right time--all you might be missing are the right tools! Let's examine the low-cost and free tools that make up my White Hat Toolbox. Ethereal Of course, every toolkit must include a network analyzer.
At BrainShare, I put aside my expensive analyzer solutions with their bells and whistles and I worked almost exclusively with Ethereal throughout the show. As a free protocol analyzer, Ethereal captures traffic, offers solid decodes and some customization. I did begin twitching after a day or so--I missed my charts, graphs and simple filtering system. In an effort to put together a truly inexpensive toolkit, Ethereal would be the analyzer of choice. You can use a network analyzer to determine if you have unencrypted data crossing your network, troubleshoot network communications and even measure latency on the network. Although typically pigeon-holed as a troubleshooting tool, your network analyzer can also be used to test the security of an application.
During another recent onsite visit, I tapped into a large medical network that had thousands of medical records flowing in clear text to and from numerous connections--frightening when you consider that the United States passed the Health Insurance Portability and Accountability Act (HIPAA) in 1996 which imposes a fine of US$25,000 per incident for each privacy violation. HIPAA is similar to Europe's 'Directive on the Protection of Individuals with Regard to the Processing of Personal Data and on the Free Movement of Such Data,' which was adopted in 1995. In Figure 1, I have used Ethereal to capture a plain-text password crossing the wire. You can clearly see SpamKiller (a spam-elimination tool by McAfee Security) sending out the POP password in plain text. I configured the password as 'seethecleartextpassword?' In this example because I wanted the password to really stand out in the trace file.